you must maintain basic privacy of whatever you are posting or sharing on your accounts. it is better to ensure security and privacy as much as possible.
...Category: Security
How To Ensure Data Security While Sharing Information
Data security is extremely important in terms of financial status and business reputation. Hence, you must implement the above steps as soon as possible.
...How To Stay Safe From Internet Security Threats
Nowadays, most people become internet-savvy. Be it personal or professional purpose, the internet is undoubtedly an integral part of today’s generation. However, convenience comes with various security...
Six Ways Hackers Can Access Your System
Hackers try to win the trust of the victim by pretending themselves as a genuine source. Clicking on the phishing link leads the person to a fake website
...How To Ensure Data Security In Cloud Computing
There is no doubt that cloud computing comes with some incredible benefits. However, companies take proper steps to safeguard their data in the network.
...Drawbacks of Antivirus Software
you may be thinking about using an antivirus tool in your system. However, it is essential to know about their potential drawbacks prior to opting for one.
...What Is Data Breach And How to Prevent It
A data breach is an unauthorized data access by any culprit/program. It can harm businesses, their customers and individuals in various ways.
...Malware Apps are more common than you think on android play …
Google is one of the biggest and most popular search engine company in the world and Android is the mobile operating system developed by Google. It is an open-source operating system. Open source means...
What Is Firewall, Its Uses and importance
Firewall is defined as a network security protocol which monitors, filters and controls traffic on a network system. A firewall happens to protect a network or PC against unauthorized access, use or...
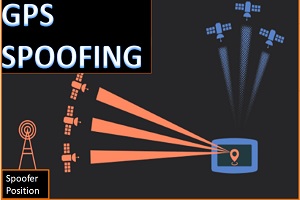
What is GPS Spoofing?
What is GPS:- Global Positioning System (GPS) is a radionavigation system, which is satellite-based. It is one of Global Navigation Satellite Systems (GNSS). GPS is owned by United States of America,...